If you haven’t yet checked out the Verizon 2024 Data Breach Investigations Report, it’s worth a look—even if you’re not a cybersecurity expert. This report is a comprehensive guide that highlights the cyber threats facing organizations and how to respond. While the report stretches over 100 pages, don’t worry—we’ve got you covered. We’ve sifted through the details to bring you the key insights that are particularly relevant for our customers and other small to medium-sized businesses. Let’s get started.
Ransomware: The Biggest Threat
You might have heard the saying, “There’s nothing new under the sun.” This holds in the world of cybersecurity, where cybercriminals are perfecting rather than reinventing their strategies. Traditional ransomware attacks are evolving to become more sophisticated and harder to combat.
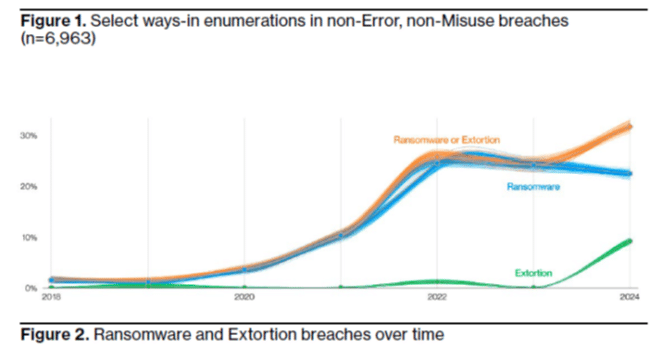
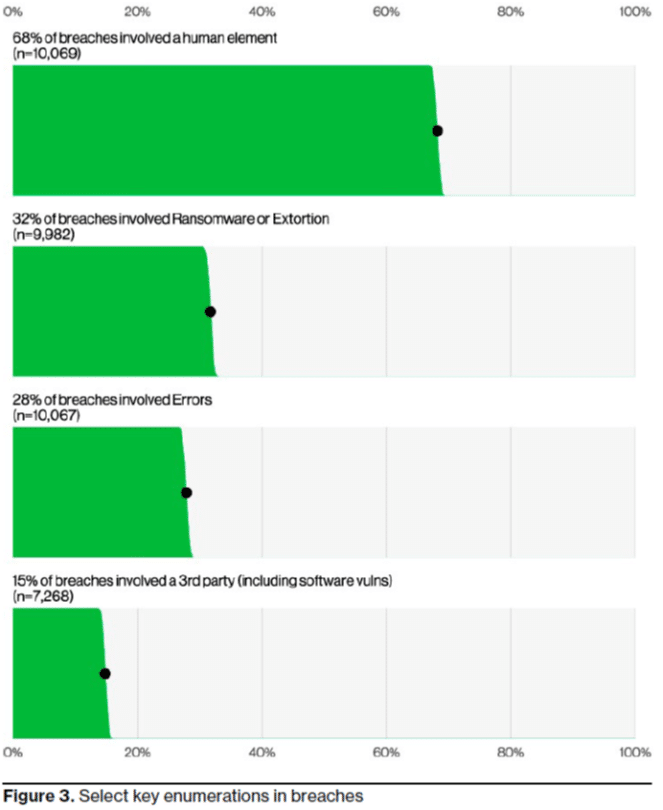
IT professionals and businesses across all industries face an ongoing battle against these threats. Cybercriminals often use a mix of hacking and malware, exploiting web applications as common entry points. About one-third of all data breaches involve ransomware or extortion, making it a prominent threat in 92% of industries.
The persistence of these tactics can be attributed to their profitability. Ransomware and extortion represent between 59% and 66% of all financially motivated attacks. As long as these methods remain lucrative, they will continue to be preferred by cybercriminals.
Third-Party Vendors: A Growing Concern
The security of your business partners is increasingly vital. Breaches related to third parties, such as affected partner infrastructures or vulnerabilities in the software supply chain, are on the rise. This year, these types of breaches account for 15% of all incidents, a 68% increase from the previous year. This surge is primarily due to the increased use of zero-day exploits in ransomware and extortion attacks.
This situation highlights a critical point: if a software provider like Microsoft has a vulnerability, it could jeopardize your systems and data. To mitigate these risks, it is essential for organizations to thoroughly research potential vendors and prioritize those with strong security measures in place. Choosing the right partners can significantly protect your business from emerging cybersecurity threats.
Social Engineering: Business Email Compromise Is Costly
Phishing and pretexting via email are major threats, accounting for a significant portion of incidents in social engineering. Pretexting often leads to what’s known as Business Email Compromise (BEC), which exploits our natural tendency to trust and assist others.
What is pretexting?
Pretexting is a tactic where attackers create a fabricated scenario or identity to obtain sensitive information or influence someone into taking an action, like transferring funds.
BEC attacks have a substantial financial impact. In these schemes, attackers might hijack an ongoing email conversation and trick victims into redirecting payments, such as updating banking details for a deposit. Despite the costs not increasing significantly since last year, they remain substantial with the median loss hovering around $50,000.
If you fall victim to such a scam, it’s crucial not to ignore it or be paralyzed by fear. Promptly reporting the incident to law enforcement is essential. According to Verizon, in half of the reported cases, victims were able to recover 79% or more of their losses. However, in 18% of the incidents, no funds were recovered, leading to total losses.
The Human Element: Redefining Security Responsibilities
As AI and cybercriminals advance their social engineering tactics, mitigating these risks remains a formidable challenge.
As the report says, “It’s much easier to harden a system than it is to harden an individual.”
The human element—whether it’s falling victim to a social engineering attack or making other errors—continues to be a primary factor in data breaches. Human error contributed to 68% of breaches, consistent with last year’s findings. Mistakes happen. After all, we are only human. However, recurring mistakes signal a deeper issue.
Given this, it’s crucial to take a moment to reassess our attitudes and beliefs about our role in cybersecurity. If leadership treats cybersecurity as merely a checkbox item, employees are likely to adopt a similar approach. Employees need to understand what is expected of them. Clear policies should be in place, outlining proper channels for reporting issues and specific actions they are responsible for.
A Glimmer of Hope: User Awareness Training Works
There’s a glimmer of hope in addressing the human element of cybersecurity. According to data from security awareness exercises in 2023, 20% of participants reported phishing attempts during simulations, and 11% of those who clicked on a phishing email reported the incident. This indicates that user awareness training is effectively enhancing vigilance.
Despite the availability of interactive training programs, there is still a significant need for improvement. Implementing these programs more broadly could strengthen an organization’s defenses. The urgency for effective training is underscored by the concerning statistic that it takes users just 21 seconds to click on a malicious link after opening an email, and only 28 seconds more to start entering their data on a phishing site. In total, users typically fall for phishing emails in less than 60 seconds.
From Statistics to Strategy
The Verizon 2024 Data Breach Investigations Report makes one thing clear. While all businesses can take steps to minimize human errors, remember this is only part of the solution. The same technology that poses threats can also defend us, turning our potential weaknesses into strengths.
It’s essential not just to close any open doors but to proactively go after these threats, use tools like MFA, and continuously monitor your network.
Cybersecurity Services in Rochester, NY, and Surrounding Areas
Collaborating with a managed IT service or cybersecurity firm can help bridge any security gaps. No one should tackle cybersecurity alone. At Just Solutions, we are committed to equipping businesses with the necessary technology to operate securely and confidently online. If you’re looking to enhance your cybersecurity measures, contact us to start with a comprehensive network assessment. We’ll help identify your vulnerabilities and discuss solutions to fortify your defenses.

